.jpg)
Whatsapp is one of the most widely used Smartphone messenger till today. It has various features like real time messaging, media sharing, group chatting and so on. Apart from this, Whatsapp also offers some hidden features that most of the people don’t know. Have you ever wondered how to recover deleted Whatsapp messages? The answer would be probably ‘yes’. Most of the times we delete our Whatsapp conversation and then after sometime we realize that we accidently deleted an important message. So today we are sharing a comprehensive guide on how to recover deleted Whatsapp messages using Whatsapp backup and restore feature.
How To Recover Deleted Whatsapp Messages:
Recovering deleted Whatsapp messages is very simple, you don’t need to be a geek in order to retrieve deleted Whatsapp messages, anyone without heavy computing and programming knowledge can recover deleted Whatsapp messages easily. So without taking much of your time here we go.
Recovering Recent Whatsapp Messages(Less than 7 Days old):
It’s very simple to recover Whatsapp chat history that is less than 7 days old. Every day at 4 am Whatsapp automatically creates a backup file of your chat history at your memory card. You can then use that backup file to recover deleted Whatsapp messages.
To make use of that backup file, just uninstall the Whatsapp messenger and then install it again, after installation, Whatsapp will ask you to Restore, Click on restore and you are done. All the chat history that is less than 7 days old will again start to appear on your Whatsapp messenger.
Recovering Old Whatsapp Messages (More than 7 days old):
Recovering old Whatsapp messages is bit complicated, Before you begin recovery, Please note that all the recent chats before particular backup will be lost upon restoration. Here are the steps to recover your old Whatsapp chat history.
1) Download and install a file manager from Google play.
2) Uninstall Whatsapp messenger.
3) Now using that file manager Navigate to /sdcard/WhatsApp/Databases folder.
4) You will find some files in that folder, as you can see in the snapshot below.
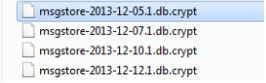
5) Select any particular date file which you want to restore and rename it to msgstore.db.crypt
i.e: Rename msgstore-2013-12-05.1.db.crypt file to msgstore.db.crypt.
6) Install Whatsapp messenger again, and choose restore when prompted. The backup file msgstore.db.crypt is restored and viola, your deleted Whatsapp messages is restored again.
So, here comes the end of article on how to recover deleted Whatsapp messages. I hope you all would have liked the article. In case of any query or suggestion please drop your valuable comments in comment box below.
Keep visiting








